Entra.News #17: Your weekly dose of Microsoft Entra
MAM for Windows and custom attributes in the Microsoft 365 profile card go GA, sync cloud groups to on-prem in near real-time (preview) and heaps more...
👋 Hi, Merill here with the seventeenth edition of entra.news and all the latest happenings in the world of Microsoft Entra. Enjoy!
⚡️ Microsoft
✅ Generally Available
Configure group claims for applications by using Microsoft Entra ID • Microsoft Learn
Mobile Application Management (MAM) for Windows using Microsoft Edge • Microsoft Learn
Microsoft Entra Privileged Identity Management (PIM) for Groups API • Microsoft Learn
Add or remove custom attributes on a profile card using the profile card API • Microsoft Learn
🔥 Public Preview
Govern on-premises Active Directory(Kerberos) application access with groups from the cloud • Microsoft Learn
ID Governance: MyAccess overview page • Microsoft Learn
ID Protection: remediate user risk through on-premises password reset • Microsoft Learn
Microsoft Entra Verified ID: Quick setup • Microsoft Learn
📖 Read
Microsoft Entra ID Governance licensing for business guests • Kaitlin Murphy
📺 Watch
The 425Show: Microsoft Entra Internet Access & Microsoft Entra Private Access (1 hour) • Nick Wryter, Jeevan Bisht
From the community…
☀️ Read
🔑 Authentication
#TalesFromTheCyberFront: Passwordless and Why It Matters • Kay Daskalakis
Login to M365 Services Using Email As An Alternate Login ID – EMS Route • Shehan Perera
Navigating Azure Identity Solutions: From Active Directory to Microsoft Entra ID -Part 1 • Sami Younis
Setup Azure File Share with Entra ID hybrid identities • Cor Den Boer
Workload ID
Continuous Access Evaluation for Workload Identities • Praba
🤖 Automation & DevOps
Monitor Entra Conditional Access with M365DSC and Azure DevOps • Will Francillette
Code Your Way to Security: Terraform and Conditional Access for Phishing-Resistant Authentication • Manish Periwal
Protect Microsoft 365 Break Glass Accounts with Azure Automation • Daniel Bradley
🖥️ Devices
The next step in a passwordless Windows experience • Peter Klapwijk
Why protecting BitLocker Recovery key retrieval is so important • Rahul Jindal
⚒️ Toolkit
ROADTools • Dirk-jan Mollema
Collect information in Entra ID with AzureADRecon and hunt with Microsoft Sentinel! • Tom Wechsler
📺 Watch
I Stole a Microsoft 365 Account. Here's How (20 min) • John Hammond
Managing and Changing Passwords in My Security Info (2 mins) • RioCloudSync
Entra App registration - Step-by step part 2 (14 mins) • BlueScreen Brothers
👨🏽💻 Merill’s corner
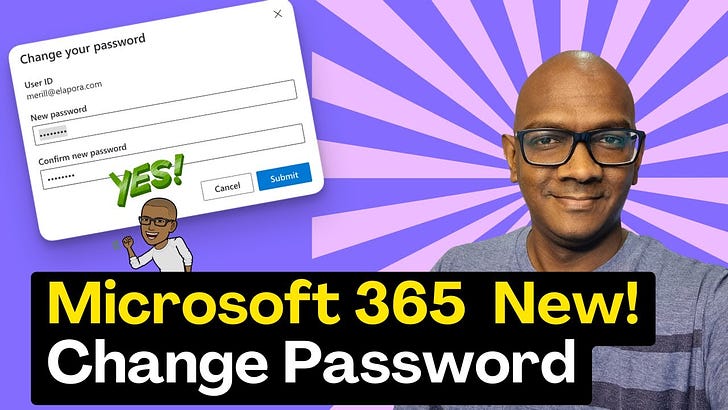
→ A new way to change passwords in Entra ID
→ Entra ID App Authentication Decision Tree
Here's a decision tree to help developers and admins who manage Microsoft 365, Azure and Entra tenants, pick the most secure authentication method for their apps.
🎯 Managed Identities
The best option for app secrets is to not have any secrets in the first place. This way, you're app credentials can never be leaked.
Where possible, always choose to use managed identities in Azure and similar features in other platforms like AWS and GCP.
Did you know that with Managed Identities in Azure, no one, including the Global Administrator, can access the underlying credential?
With managed identities, identities are provided and deleted with Azure resources.
Managed Identities with Azure Arc
Did you know that you can use Managed Identities on Azure Arc enabled servers running on AWS, GCP and another other cloud or on-premises environment?
Learn more at Authenticate against Azure resources with Azure Arc-enabled servers - Azure Arc.
🎯 Workload Identity Federation
With workload identity federation, you can set up Microsoft Entra ID to trust 3rd-party identity provider tokens from services like AWS, GitHub, and Google Cloud.
For example, using this approach, an app running on AWS with an identity in Amazon Cognito can present its Cognito token to Entra ID to access Entra-protected resources like Azure OpenAI or Microsoft Graph.
🎯 Certificates
Not all services in Azure support Managed Identities yet, and there maybe instances where workload identity federation might not be an option.
The next best method is to use certificates for app authentication.
When using certificates, you are responsible for using short lived certificate expiry, protecting the private key from being leaked and rotating the cert when it expires (or if there is a compromise).
You also need to worry about application outage while the cert is being rotated (unless your devs add support for multiple active keys).
🎯 Client ID & Secret
This is by far the most used app authentication method because of its simplicity. Unfortunately, this is also the reason credentials are leaked quite easily and unintentionally.
Dangers include secrets checked into code, secrets left lying around on unencrypted text files, etc. Leaked credentials grant easy access to your data to threat actors.
Where possible, help your devs and vendors move off client secrets to using stronger authentication like managed identities and certs.
🎯 Learn more
➡️ To learn more about avoiding common app-related security pitfalls, see this recent post by Brian Melton-Grace.
Public vs. confidential clients and how to avoid common security pitfalls in identity | Microsoft Entra Identity Developer Blog
➡️ To learn about workload identity federation, see Workload identity federation | Microsoft Learn
Note: Some of these advanced workload protection capabilities require a Workload ID Premium licence for each app. See the FAQ page linked above for details.
→ cmd.ms
It's hard to believe that a year has gone by since I launched cmd.ms 🍾
Here are some awesome stats 👇. Many thanks to everyone that has contributed to make this is a success and to all you keyboard ninjas 🥷!
→ Entra ID Governance Guest License
Folks, there's an updated pricing for the new Microsoft Entra ID Governance license for guests. Read the blog post for details.
It will be based on monthly active guests, and you get to use all the cool new ID Governance features with guest users.