Entra.News #14: Your weekly dose of Microsoft Entra
👋 Hi, Merill here with the fourteenth edition of entra.news and all the latest happenings in the world of Microsoft Entra. Enjoy!
⚡️ Microsoft
✅ Generally Available
Microsoft Admin Portals in Conditional Access • Microsoft Learn
🔥 Public Preview
Microsoft Graph Activity Log is Now Available in Public Preview • Kristopher Bash
Delegate the Azure role assignment task to others with conditions • Microsoft Learn
📖 Read
Require multifactor authentication for Microsoft admin portals • Microsoft Learn
Step-by-Step Guide to Identify Inactive Users by using Microsoft Entra ID Governance Access Reviews • Dishan Francis
From the community…
☀️ Learn
Microsoft's Identity Revolution: From Azure Active Directory to Microsoft Entra ID • Adrian Buxton
🥷 Security
Detect threats using Microsoft Graph Logs - Part 1 • Fabian Bader
Phishing for Primary Refresh Tokens and Windows Hello keys • Dirk-jan Mollema
⛑️ ID Protection
Leaked Credential Detection Report in Microsoft Entra ID • Sudha
🔑 Authentication
A zero-disruption path to better MFA • Chris Beattie
🖥️ Devices
Easily hiding the ability to use passwords for signing into Windows • Peter van der Woude
🤖 DevOps
How to Block PowerShell for Microsoft 365 Users • Tony Redmond
How to Create Dynamic Microsoft 365 Groups (and Teams) for Departments • Tony Redmond
How to Remove Licenses from Disabled Accounts • Tony Redmond
How to Report Microsoft 365 Licenses Assigned through Group-Based Licensing • Tony Redmond
How to Bulk Update Microsoft 365 Groups Owners with PowerShell • Daniel Bradley
How to Output Invoke-MgGraphRequest Responses as a PowerShell Object • Daniel Bradley
♻️ Sync
Active Directory Health Check using Microsoft Entra Connect Health Service • Przemyslaw Klys
⚒️ Toolkit
EntraID-MFA-DynamicGroup • Dominik
🎙️ Podcasts
Ctrl+Alt+Azure | 207 - What is Microsoft Entra ID cross-tenant sync? • Jussi Roine, Tobias Zimmergren
Let’s Talk Azure | S4E18 - Microsoft Entra External ID - Provide access for external identities to you application or tenant • Alan Armstrong, Sam Foot
📺 Watch
How to use Temporary Access Pass in Microsoft Entra ID! (10 mins) • Peter Rising MVP
Web sign-in for Windows (Globally Available!) (5 mins) • RioCloudSync
Goodbye Passwords! Hello Passkeys (11 min) • Andy Malone
👨🏽💻 Merill’s corner
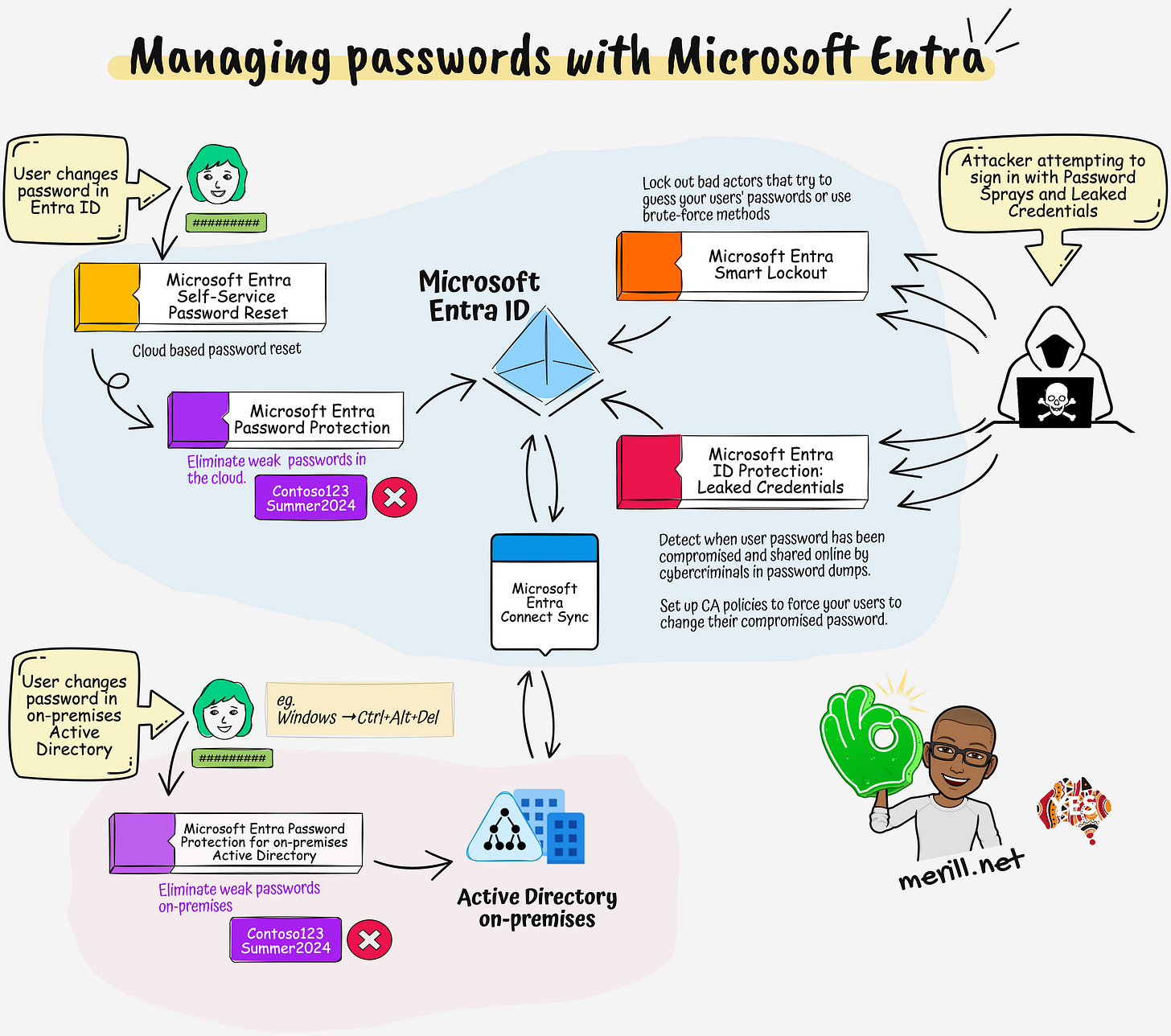
While we are HUUGE fans of passwordless at Microsoft, Microsoft Entra has some awesome capabilities to manage and protect your user's passwords. I recently came across a few posts on Reddit and Twitter where there was some confusion around features like Password Protection and Leaked Credential Detection.
I'm hoping this one-pager will help clarify this topic.
🎯 Microsoft Entra Self-Service Password Reset (SSPR)
This is a cloud-based password reset feature that allows users to change their password. Once setup, get your users to browse to aka.ms/sspr or aka.ms/mysecurityinfo whenever they need to change their password.
License: Requires M365 Business Premium or Entra ID P1/P2 for on-prem users
Learn more: Enable Microsoft Entra self-service password reset • Microsoft Learn
🎯 Microsoft Entra Password Protection
Stop your users from setting weak passwords like <companyname>123 or Summer2023 or other weak combinations such as your brand or product names. This is enabled by default when you enable SSPR. Make sure you customize the banned password list to add your company name, abbreviations and other easy to guess words.
License: Global banned lists available on all tenants while custom banned list and on-prem synced users requires Entra ID P1.
Learn more: Eliminate bad passwords using Microsoft Entra Password Protection • Microsoft Learn
🎯 Microsoft Entra Password Protection for Active Directory Domain Services
This is a neat add-on that you install on-prem to bring the same Entra Password Protection capabilities to your on-prem AD. You will no longer need to worry about users setting weak, easily guessable passwords on-prem.
License: Entra ID P1
Learn more: Enforce on-premises Microsoft Entra Password Protection for Active Directory Domain Services • Microsoft Learn
🎯 Microsoft Entra Smart Lockout
Smart lockout helps lock out bad actors that try to guess your users' passwords or use brute-force methods to get in. Smart lockout can recognize sign-ins that come from valid users. Attackers get locked out, while your users continue to access their accounts and be productive.
How smart is that?
License: Available out of the box on all tenants but customizing settings requires Entra ID P1 or higher.
Learn more: Prevent attacks using smart lockout • Microsoft Learn
🎯 Microsoft Entra ID Protection: Leaked Credentials
Detect when user password has been compromised and shared online by cybercriminals in password dumps.
Set up risk based conditional access policies to automatically guide impacted users to change their compromised password.
License: Leaked credential detection is available on all tenants while Risk Based CA policies to auto-remediate requires Entra ID P2.
Learn more:
Leaked credentials • Microsoft Learn
User risk-based password change • Microsoft Learn