Entra 🆔 News #118 → This week in Microsoft Entra
Learn about public preview of transfer user Source of Authority (SOA) to the cloud plus more!
👋 Hi, Merill and Joshua here with this week’s roundup of the latest news on Microsoft Entra from around the globe 🌍.
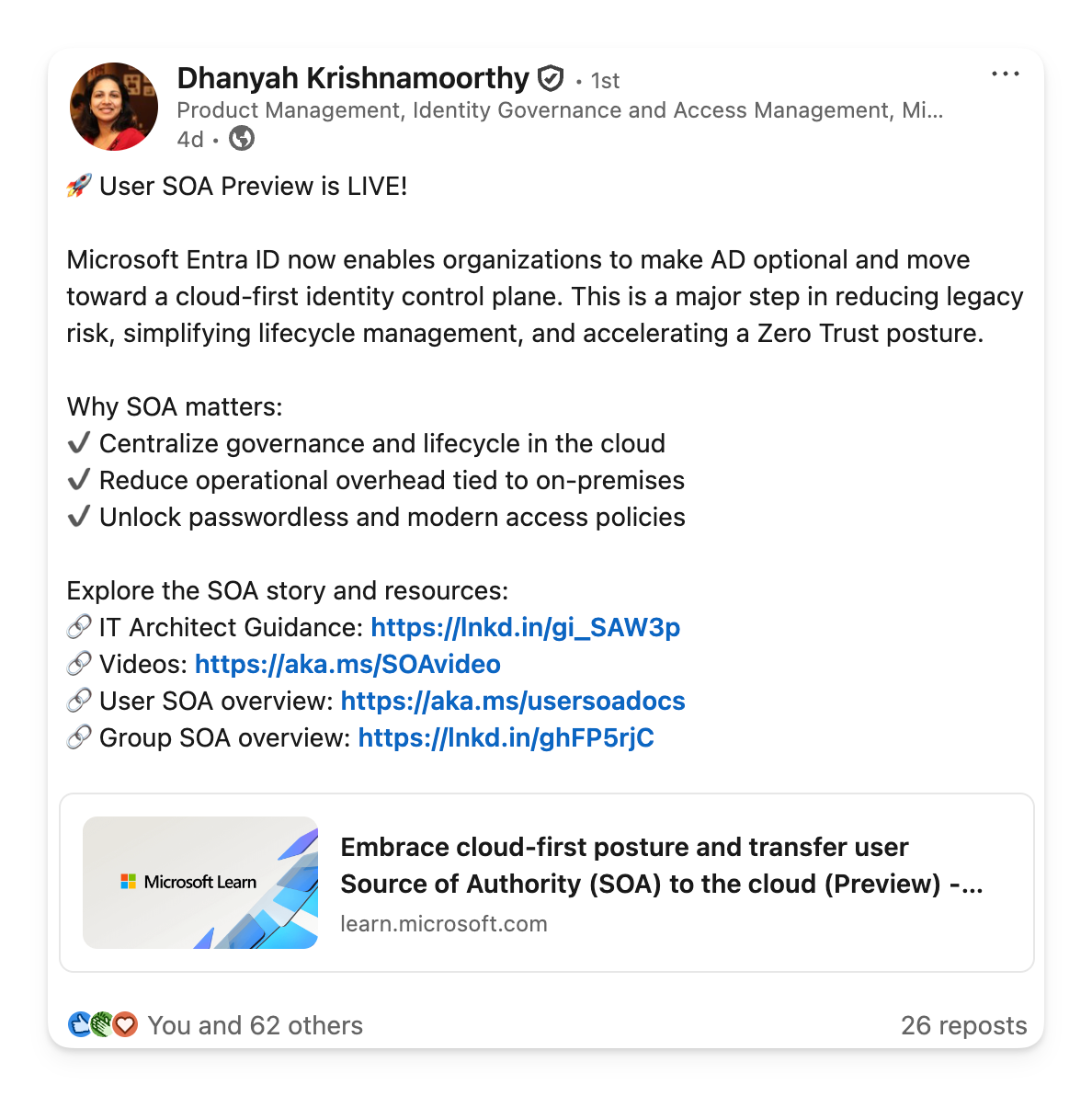
The big news this week is the transfer user Source of Authority (SOA) to the cloud. This feature was years in the making and allows you to transition user identities from being mastered from on-prem AD to Entra ID.
In case you missed the live Entra AMA from earlier this week, don’t fret. You can catch up on this week’s Entra Chat podcast, we had a lively conversation, the questions kept coming with 100+ of you joining in live.
Why AI Is Breaking Identity Security – Experts Spill the Truth!
Welcome back to Entra.Chat! In this rapid-fire Q&A, I’m joined by a team of brilliant CXE Identity Architects from Microsoft, and they’re answering the toughest questions on the future of identity.
Enjoy!
Sponsored by:
Shadow IT and SaaS sprawl are growing faster than IT & Security teams can keep up
Most organizations face these universal app governance challenges:
📦 Entra ID isn’t secure by default
💥 SaaS adoption won’t slow down
⌨️ Citizen Development keeps rising (hello, Copilot Studio!)
🗑️ Vendors often don’t remove apps after uninstall
🔃 Offboarding & ownership are inconsistentENow AppGov Score shines a light on hidden risks and provides a free Application Governance Assessment Report so you can spot over-permissioned apps, reclaim control, and protect your environment from breach and disruptions.
⚡️ Microsoft
🔥 Public Preview
Embrace cloud-first posture and transfer user Source of Authority (SOA) to the cloud (Preview) - Microsoft Entra ID • Microsoft Learn
📖 Read
Transforming our VPN with Global Secure Access at Microsoft • Leon Yen
Disrupting threats targeting Microsoft Teams • Microsoft Threat Intelligence
Your shortcut to Microsoft Entra deployment success • Brooke Robertson
📺 Watch
How to move Active Directory Source of Authority to Microsoft Entra ID and why (10 min) • Microsoft Mechanics
Sponsored by:
🔐 Explore Azure with a Risk-Based View of Threats
As an Entra ID user, you’re already focused on identity but what about the rest of your cloud? Data, APIs, and services all introduce hidden risks.
You can now try the new TrustOnCloud demo platform, no setup, no forms, just explore.
Inside, you’ll find:
✅ ThreatModels for Microsoft Azure storage
✅ Data flows, threat scenarios, and mapped controls
✅ A visual, intuitive way to explore cloud risks
✅ A preview of how we cover AWS and Google Cloud too
From the community…
🚀 Most popular posts from last week
🥇Microsoft Introduces Restore Capability for Conditional Access Policies • Tony Redmond
🥈Why Setting Office IP as a Trusted Location in Conditional Access Is Risky • AIMA
🥉Microsoft Entra ID applications: Why Ignoring Them Could Cost You • Sander Berkouwer
☀️ Learn
👩✈️ AI & Copilot
Entra Agents are Promising but Could do More • Tony Redmond
Workday and Microsoft to Deliver Unified AI Agent Experience for the Enterprise • Workday
👮♂️ ID Governance
🌐 Private Access & Internet Access (GSA)
How to Enable and Test Threat Intelligence Policies in Microsoft Entra Global Secure Access • Sreejith Reghunathan Pillai
Unify Identity and Network Access for Zero Trust Security • PaVee
📦 Apps
How to Get Entra Enterprise Application Permissions Report • Lokesh
Secretless confidential applications • Stephan Van Rooij
🔑 Authentication
Entra ID phishing-resistant MFA a staged rollout • Mark Oldham
👥 User & Group Management
The Trojan Horse in Your Microsoft 365 Tenant • JJ Milner
🤖 DevOps & PowerShell
New Graph API methods available for Entra ID audit logs operations • Vasil Michev
Sync-EntraUserState • Marco Wohler
🚦 Conditional Access
Conditional Access Essentials: Custom Security Attributes in Entra ID and Cross Tenant Scenarios • Ewelina Paczkowska
Configure Conditional Access Policies to Protect Generative AI Apps in Microsoft 365 • Blesslin Rinu
Understanding Sign-In Frequency (SiF) in Hybrid-Joined Environments • Gabriel Delaney
Entra ID – Soft-delete & Restore for Conditional Access + New PowerShell Module • Michael Morten Sonne
How to restore deleted Entra ID Conditional Access policies and Named Locations • Jan Bakker
Restoring Microsoft Entra Conditional Access Policies • Philip Marsh
Secure Cloud Foundation: The Customer Conversation • Jon Hope
📺 Microsoft Adds Restore to Conditional Access – Here’s Why It Matters (5 min) • RioCloudSync
🖥️ Devices
How to Enable Firefox SSO using Intune • Prajwal Desai
🏙️ External ID - Guests & Multi-Tenant Organizations
Switching SharePoint To Use Entra Guest Sharing With EnableAzureADB2BIntegration $true • Brian Reid
Windows 365 and the External Identity preview – using a guest account to access Cloud PCs • Paul Winstanley
Windows 365 and the External Identity preview – using a guest account to access Cloud PCs • Niall C. Brady
📺 How to setup Windows 365 Cloud PCs for guest users (12 min) • Get Rubix
♻️ Sync
AD Mobile Number Not Syncing to Entra ID? You’re not alone • Moe Kinani
📺 How to Change Source Of Authority in Entra ID & Graph Editor • Andy Malone
📒 Tenant Configuration
⚒️ Toolkit
Migrate2GSA Toolkit • Global Secure Access Community → Andres Canello
🎙️ Podcasts
📺 One Token to Rule Them All? Azure Security, AI Agents & Certifications Unpacked | EP21 (51 min) • Cloudy with a Chance of Insights, The MSFT Podcast
🔥 Maester
👨🏽💻 Merill’s corner
Want to get featured on Entra.News? → Submit your content 😎
Want us to say nice things about your company? Sponsor entra.news 🤩
Love the newsletter? Tell us 💚❤️💜
🪃 Acknowledgement of Country
Entra.News is created on Wurundjeri land and acknowledges the traditional owners of country throughout Australia, recognising their continuing connection to land, water and community. We pay our respect to them and their cultures and to elders both past and present.






This is such a comprehensive roundup! The transfer user Source of Authority to the cloud feature is absolutly game-changing - this has been a pain point for hybrid organizations for years. I'm excited to see how this simplifies identity management workflows. The Microsoft Mechanics video on SOA transfer is really helpful for understanding the practical implementation. Also appreciated the community contributions section, especially Tony Redmond's piece on restoring Conditional Access policies - that's a critical capability that was missing before. Great curation as always!